
Authentication is verifying if the user logging in is the owner of the account. Multi factor authentication is verifying the user in multiple steps. The most popular way of primary or first level of authentication is the username-password method. This can be very risky, as the username will most probably be email addresses, and passwords, which can be often guessed by hackers. Hence, you sould ensure that you have set a strong password that is complicated to break and passwords have to be stored in encrypted format in your databases so that it gets additional protection.
Few measures to be taken to ensure stronger passwords:
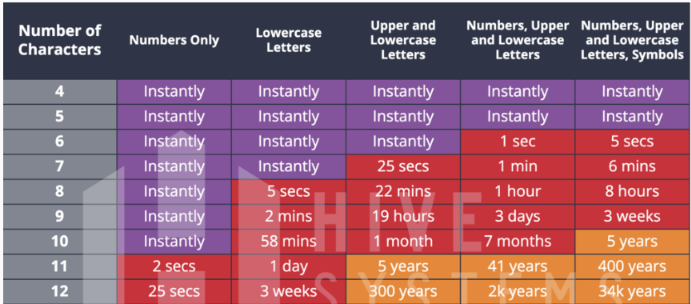
- Length of password: Each additional character in your password increases the complexity exponentially. So passwords should have a minimum of 8 characters. For example, hello is easier to crack than 4lp4b3t4@
- Character sets: Each character set has a certain number of permutations. Select a password that is a mix of lowercase & uppercase letters, digits 0-9, and special characters like @#$%, etc. For example abcdef is easier to crack than d3lt4@g4mm
- Common words: A computer can run a “dictionary attack” against a password very quickly, checking for all real words. hence avoid common words. For example, potato is easier to crack than d3lt4@g4mm
Your password should be more than 8 characters and should contain a combination of both upper and lower case letters, a number, and special characters to increase complexity. See below a chart that shows the time to crack passwords of different complexity levels.
Additional Security with Multifactor authentication
As per a study conducted by Verizon Data Breach Investigation Report, 81% of data breaches are due to poor passwords. Password vulnerabilities like weak passwords, reusing of passwords, etc are common reasons for the hacking of systems. Hence, multi-factor authentication becomes even more relevant and blocks 99.99% of attacks.

Multi factor authentication or MFA is a security approach that requires users to validate their identity with multiple authentication factors. As described above, when you sign into your account your identity is confirmed by the first authentication factor, which could be your username and password. This will be single-factor authentication and has a lower level of security. For additional security, you can add a second authentication factor that again reverifies the user. Thus, with multi factor authentication an extra layer of protection is added to the verification process. This makes it more difficult for hackers to obtain access to the accounts.
For example, if a second layer of authentication, in the form of a one-time passcode (OTP), is sent to the user’s phone. It will be difficult or rather impossible for hackers to break into, as they do not have access to the phone in which the passcode is being sent. This is double protection.
Common types of Multi factor authentication
There are several methods of multi factor authentication in use today; some are stronger or more difficult than others, but they all provide better security than simply using a password.
- Phone one-time-passwords(OTP)
Here the second factor of authentication will be through your registered mobile number. You will receive an OTP as an SMS, a link, or a call, which has to be entered after the first level of authentication. You will be able to access your account only once this second level of authentication is completed. Below are the phone authenticators:
- A one-time-passwords(OTP) that is received as an SMS on your registered mobile number.
- An SMS link that is received as an SMS on which you need to click Allow/Deny.
- A one-time-passwords(OTP) that is received as a voice call on your registered mobile number.
- Authenticator Apps
In this method, you need to link your authenticator app by scanning a QR code to link it to the application. After the linking process, the authenticator app will provide a time-based one-time password (OTP). This OTP token has to be entered to complete the second level of authentication. Few popular authenticator apps are:
- Google Authenticator
- Microsoft Authenticator
- Auty Authenticator
- Hardware Token
A hardware token is in the form of a small device. In this method, you will need to plug the device into your computer. On the trigger of a button, it sends a unique code that does the authentication. These forms of authenticators are easier for users, and harder for hackers to crack. The most popular USB authenticator is Yubikey tokens. Listed below are the popular hardware authenticators:
- Yubico Yubikey
- Google Titan Key
- Thetis FIDO Security Key
4. Email OTP
Here the second factor of authentication will be through the code sent to your registered email address. You will receive a code as an email or a link, which has to be entered after the first level of authentication. Only once this second level of authentication is completed, will you be able to access your account. Below are the email authenticators:
- A one-time-passwords(OTP) is sent to your registered email address.
- An approval link is sent to your registered email address, on which you need to click Allow/Deny to proceed with the autentication.
Conclusion
Multi factor authentication is simple, easy to implement, and ensures double security to your user accounts. So ensure that wherever available MFA is promptly used.


