
The Domain Name System (DNS) is the backbone of the internet, responsible for translating human-friendly domain names into IP addresses that computers use to communicate. However, despite its essential role, DNS is not without vulnerabilities. One of the most notorious threats to DNS security is DNS Cache Poisoning, a type of cyberattack that can redirect unsuspecting users to malicious websites by injecting false DNS information into a server’s cache.
In this blog, we’ll explore the intricacies of DNS cache poisoning attacks, how they work, and the most effective prevention and mitigation strategies to protect your organization from these threats.
Understanding DNS Cache Poisoning
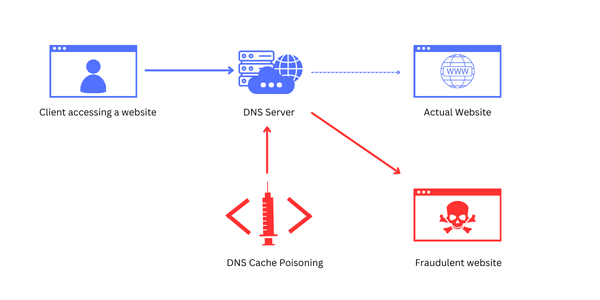
DNS, or Domain Name System, acts like the internet’s phonebook. When you type a website’s name into your browser, DNS helps find the corresponding IP address for that site. Thus allowing your browser to connect to the right server. Instead of remembering complex IP addresses, DNS translates human-friendly domain names into numerical IP addresses. These IPs computers understand, making the internet easier to navigate. When a DNS server receives a request for a domain that it doesn’t know the IP address for, it queries other DNS servers to find the correct address. Once it gets a response, the server temporarily stores—or “caches”—this information for faster response times in future queries.
DNS cache poisoning is a type of cyberattack where attackers inject false information into a DNS server’s cache. Normally, DNS servers store the correct IP addresses for websites to speed up future lookups. However, if an attacker can insert incorrect IP addresses into this cache, users who try to visit a website may be redirected to a malicious or fake site. This can lead to security issues like data theft or malware infection. Essentially, it tricks the DNS system into giving users the wrong address, allowing attackers to intercept or manipulate traffic.
DNS spoofing is also known as DNS cache poisoning. Although people often use the terms interchangeably, some argue that poisoning refers to the attack method, while spoofing describes the end result. In other words, attackers use DNS cache poisoning to achieve DNS spoofing.
How DNS Cache Poisoning Works
Here’s a simplified breakdown of a DNS cache poisoning attack:
- DNS Query: A user attempts to access a legitimate website, and the DNS resolver (typically their ISP or a public DNS service) sends out a query to resolve the domain name into an IP address.
- Intercept and Inject False Data: An attacker sends a malicious response to the DNS resolver before the legitimate DNS server can reply. The malicious response includes the wrong IP address, tricking the resolver into caching it.
- Redirected Traffic: Future requests to that domain are redirected to the IP address provided by the attacker. This often leads to phishing websites or even sites hosting malware.
- Persistence: The malicious DNS entry stays in the cache for the duration of the TTL (Time-to-Live) period. Thus affecting every user who tries to visit the legitimate site.
Why is it Dangerous
DNS cache poisoning is particularly insidious because of its scope and reach. Once a cache is poisoned, every user who queries the compromised DNS server will be sent to the attacker’s destination until the cache is cleared or the TTL expires. Here’s how they typically gain from it:
- Phishing and Data Theft: By setting up fake websites that closely mimic legitimate ones, attackers can trick users into entering sensitive information like login credentials, credit card details, or personal data. This information can then be used for identity theft, fraud, or unauthorized access to accounts.
- Financial Gain: Once attackers have access to sensitive financial data or account credentials, they can steal money directly, make fraudulent transactions, or sell the stolen information on the dark web.
- Wider Attacks: Attackers can use stolen login credentials to infiltrate corporate networks, access critical systems, or launch broader cyberattacks such as ransomware or data breaches, often causing significant damage.
- Spreading Malware: Attackers may redirect users to malicious sites that automatically download malware or spyware onto their devices. This malware can be used for surveillance, data theft, or even taking control of the infected device.
- Undermining Trust: Successful DNS cache poisoning attacks can damage the trust between users and service providers by making websites appear unreliable or compromised. This erosion of trust can harm businesses and online services.
Preventing DNS Cache Poisoning Attacks
Though DNS cache poisoning is a serious threat, several prevention measures can help reduce the risk of falling victim to such attacks:
1. DNSSEC (Domain Name System Security Extensions)
One of the most effective ways to prevent DNS cache poisoning is by implementing DNSSEC. DNSSEC digitally signs DNS responses using cryptographic keys, ensuring that the data hasn’t been tampered with. If a DNS resolver receives a forged response without a valid DNSSEC signature, it discards the response. This additional layer of security makes it much harder for attackers to inject malicious data.
2. Randomizing Query Ports and Transaction IDs
DNS queries typically use the well-known UDP port 53, which attackers can exploit by sending forged responses. By randomizing the query ports and transaction IDs, it becomes significantly more difficult for attackers to guess the correct parameters and inject false data into the DNS cache.
3. Use of Trusted DNS Resolvers
Many DNS resolvers, such as Google Public DNS and Cloudflare’s 1.1.1.1, have implemented strong security measures to prevent cache poisoning attacks. These resolvers use techniques like query minimization, DNSSEC validation, and rate limiting to detect and mitigate attacks. Using a trusted DNS resolver for your network adds an additional layer of protection.
4. Cache Poisoning Prevention (CPP) Mechanisms
Certain DNS server software includes Cache Poisoning Prevention (CPP) features, which compare incoming DNS responses to existing cache entries and drop suspicious or mismatched records. Regularly updating your DNS software to include the latest security patches and CPP features helps mitigate the risk of attacks.
5. Enforce Short TTL Values
Although not a direct preventive measure, enforcing shorter TTL values for DNS records can help minimize the impact of a cache poisoning attack. If a DNS cache is poisoned, a shorter TTL means the malicious entry will expire sooner, reducing the window of opportunity for attackers.
Mitigating DNS Cache Poisoning Attacks
In addition to preventive strategies, it’s essential to have mitigation plans in place in case of an attack. Here are some mitigation strategies to consider:
1. Regular Cache Flushing
A critical response to DNS cache poisoning is regularly flushing the DNS cache. This ensures that any poisoned entries are removed, restoring legitimate DNS responses. Automated tools can be set up to flush DNS caches periodically, reducing the lifespan of any malicious entries.
2. Monitoring DNS Logs
Proactively monitoring DNS logs for unusual activity can help detect potential poisoning attempts early. Look for patterns like unusually high volumes of DNS requests for specific domains, anomalies in DNS responses, or a sudden increase in users being redirected to unfamiliar IP addresses.
3. Implementing DNS Over HTTPS (DoH)
DNS over HTTPS (DoH) is a protocol that encrypts DNS queries to prevent attackers from intercepting and tampering with them. While it doesn’t directly address cache poisoning, DoH helps mitigate man-in-the-middle attacks that can be used to facilitate DNS poisoning. Enabling DoH on your network provides an additional layer of security.
4. Response Policy Zones (RPZs)
DNS Response Policy Zones (RPZs) allow you to create custom DNS response rules. In the event of a known poisoning attempt, RPZs can block or redirect malicious domains, limiting the damage. This strategy can also be used in conjunction with threat intelligence feeds to dynamically update your DNS policies.
Conclusion
DNS cache poisoning is a potent attack vector that can have serious consequences for organizations and end users alike. The open and decentralized nature of DNS makes it inherently vulnerable to exploitation, but by implementing strong preventive measures—like DNSSEC, query randomization, and trusted DNS resolvers—you can significantly reduce the likelihood of an attack. Additionally, preparing mitigation strategies such as regularly flushing the cache, monitoring DNS activity, and implementing response policy zones ensures a swift response to any poisoning attempts.
Ultimately, securing your DNS infrastructure is a critical step toward safeguarding your network, protecting your users, and maintaining the integrity of your online services.


